 Today’s various versions of ransomware are dangerous. By forcibly locking down important files on a victim’s computer, threats like CryptoLocker and CryptoWall are posing significant threats to both businesses and ordinary computer users. However, a new type of ransomware has appeared called CryptoJoker; and we assure you, there’s nothing funny at all about this one.
Today’s various versions of ransomware are dangerous. By forcibly locking down important files on a victim’s computer, threats like CryptoLocker and CryptoWall are posing significant threats to both businesses and ordinary computer users. However, a new type of ransomware has appeared called CryptoJoker; and we assure you, there’s nothing funny at all about this one.
Like other types of ransomware, CryptoJoker encrypts the victim’s files and issues a decryption key once a ransom has been paid. This ransom is usually demanded in bitcoin to ensure the anonymity for the one holding your data hostage. The idea is to instill fear into the hearts of the victim, so that they make the rash decision to pay hackers for the safe return of their files. Ransomware is typically distributed via email phishing scams, and CryptoJoker is no different. Victims are infected through an installer that’s disguised as a PDF file.
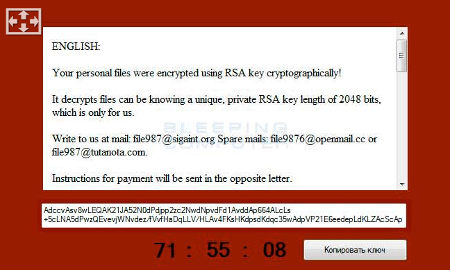
Once the user has installed CryptoJoker, the malware scans all drives connected to the infected device, including network drives. CryptoJoker looks for specific file extensions that will become encrypted. As reported by Bleeping Computer, the following file formats are targeted and encrypted by CryptoJoker:
- .txt
- .doc
- .docx
- .xls
- .xlsx
- .ppt
- .pptx
- .odt
- .jpg
- .png
- .csv
- .sql
- .mdb
- .sln
- .php
- .asp
- .aspx
- .html
- .xml
- .psd
- .java
- .jpeg
- .pptm
- .pptx
- .xlsb
- .xlsm
- .db
- .docm
- .sql
Though CryptoJoker isn’t widely distributed, it’s still a major issue that needs to be dealt with. The biggest problem with CryptoJoker is definitely the quality of its encryption. AES-256 encryption is heavy-duty, which makes it exceptionally difficult (and in most cases, impossible) to retrieve your data without paying the ransom. Supposedly, the only way to get rid of CryptoJoker is by contacting the developers and paying the ransom, so the key is to prevent it from ever infecting your network and data. If you do get infected by CryptoJoker, the solution will be relying on your data backup solution.
So, what can you do if you don’t have a backup of your data for this express reason? It needs to be understood that paying these criminals for the decryption key isn’t an option for your business. What guarantee do you have that they’ll make good on their promise and return your files to you? For all you know, they could take your money and run, leaving you with nothing but an empty wallet (we’ve seen this before with other ransomware). You should never trust a criminal to keep their word, and the developers of CryptoJoker are no different.
If you aren’t certain that your current security solution will protect you from threats like CryptoJoker, now is the time to contact Evolve IT. We can help ensure that your data is backed up properly, and equip your business with the defenses necessary to prevent the latest threats from entering your network. It’s crucial to do this before you get infected, because in cases like this, recovering the encrypted files is next to impossible.
For more information about how we can help you prevent CryptoJoker and other cyber threats, give Evolve IT a call at (518) 203-2110.

