 Cyber security continues to be a major pain point for small and medium-sized businesses, even if they’re taking the fight to the latest threats with solutions like antivirus and firewalls. Significant progress has been made, yet new threats are born every day. In fact, you might be surprised to find out that a monstrous 27.3 percent of all malware in the world was created just last year.
Cyber security continues to be a major pain point for small and medium-sized businesses, even if they’re taking the fight to the latest threats with solutions like antivirus and firewalls. Significant progress has been made, yet new threats are born every day. In fact, you might be surprised to find out that a monstrous 27.3 percent of all malware in the world was created just last year.
These results come from PandaLab’s 2015 annual report, which discusses the current state of threats in the online community:
In total, more than 84 million new samples were detected and neutralized by PandaLabs, with an average of 230,000 samples daily. We currently have 304 million samples of malware registered, which means that more than one in four of all samples ever recorded were registered in 2015 (27.36%).
PandaLabs breaks this figure down even further, sorting these threats out by category and infection type:
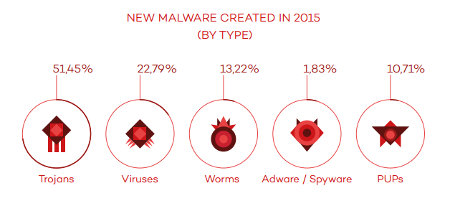
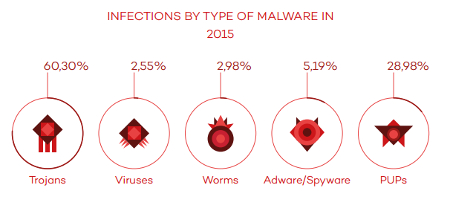
That’s a lot of threats that can potentially infiltrate your system, and the number grows daily. Therefore, it has become more important than ever to ensure the security of your business’s systems. If your organization were to be breached by malicious entities, you’re looking at incredibly dangerous and pricey fines that can break your budget. This is especially true if you work with sensitive credentials like credit card numbers and medical records, where you’re subject to regulatory compliance laws like HIPAA and PCI.
If malware is going to continue growing more powerful and prevalent over time, it makes sense to bolster your business’s security as much as possible. As the increasing number of high-profile hacking attacks prove, you shouldn’t be gambling with the future of your business’s technological assets. Fortunately, you don’t have to go about implementing solid cyber security solutions alone. The great part of being in the IT industry is that Evolve IT knows how to secure systems from threats of all kinds, and we want to share our accumulated knowledge and expertise with your business.
One solution that we wholeheartedly recommend is a Unified Threat Management (UTM) solution. The UTM is one of the most comprehensive security measures that you can take advantage of. It includes an enterprise-level firewall and antivirus solution, and augments their capabilities with proactive measures like spam blocking and content filtering tools. The end result is an all-in-one solution that’s designed to limit your business’s exposure to many different kinds of threats. Of course, there isn’t a one-size-fits-all solution for IT security, so we recommend reaching out for a consultation to determine what type of IT security would fit your business.
For more information about cyber security or UTM solutions, don’t hesitate to call Evolve IT at (518) 203-2110.

